The cyber-physical security of any manufacturing system, specifically food and drug manufacturing, is essential. The technology in the pharmaceutical industry advanced significantly in last decade to improve upon every aspects of drug manufacturing. However, much less attention has been paid to identify and proactively mitigate the risk of cyber-physical attacks. Viruses that threaten these systems are very real and in recent years have proven very harmful and costly. Those that target drugs consumed by billions of people worldwide will inevitably have deadly consequences. Even with dedicated IT departments focused on determining cyber-physical attacks, it is imperative that a base layer of protection should be integrated into pharmaceutical manufacturing plants for the well-being of manufacturing system as well as consumers. This paper gives the overview of methods and tools useful for cyber-physical security of pharmaceutical manufacturing processes.
The cyber-physical security is no longer an area that should be overlooked. Unfortunately, cyber-physical attacks of all kinds may cost companies a great amount of money and countless lives. In a recent PharmaIQ report, an increasing trend of ‘cyber-physical security risk’ has been found.Therefore, a systematic framework is needed to mitigate the risk of cyberphysical attacks.
Pharmaceutical plants need to employ security measures in order to lay the foundation of a comprehensive cyberphysical security plan. These measures will be the integration of cyber-physical security tools into the pilot-plant network in order to prevent and deter infiltration. It should be noted early on that the Work Station (WS) computer should not be used for any purposes outside the scope of the manufacturing plant to minimise risks of possible cyber-physical attacks. This includes trivial activities such as checking emails and surfing the web because after all, the most common type of cyber-physical attacks are malicious software downloads caused by clicking seemingly harmless links and attachments.
The direct compaction pilot plant at the Engineering Research Center for Structured Organic Particulate Systems (C-SOPS) at Rutgers comprises of three different levels which utilise gravity as the main force responsible for transporting powders from and to each step of the process. The top floor holds the feeders that discharge API and excipients. The middle floor holds the mill, blender and lubricant feeder. The ground floor contains the final operation unit, the tablet press. The more details of the pilotplant can be found in Singh et al. (2014). In the pharmaceutical Manufacturing Plant, the local host belongs to the desktop computer that is referred to as the work station. The work station’s network is shared by the PLC, unit operation, and the Windows Server that runs control software.
A systematic framework for cyber-physical security of pharmaceutical manufacturing process is shown in Figure 1. The pharmaceutical industry needs protection with expansion into cyber-physical defense as it can be integrated into the plant. The need of some of the tools such as network traffic analyser, file integrity monitoring tool, and data block monitoring tool are highlighted in the figure. A novel Cyber-physical Security (CPS) tool (developed in-house) is also shown in the figure. The pharmaceutical manufacturing plant is typically connected to various software/hardware via numerous pathways. The PLC is the industrial computer that allows control of the pharmaceutical manufacturing process. All unit operation except the tablet press of the plant is connected to the PLC via Profibus or a serial port. The tablet press is connected to the PLC by an OPC protocol, using OPC Scout. The work station has installed a Distributed Control System (DCS), a software that allows high level programming control as well as visualisation of the entire process. The work station also provides a center for which all IT and process data can be monitored and controlled as well as host the plant specific CPS Tool integrated into the plant. (Figure 1)
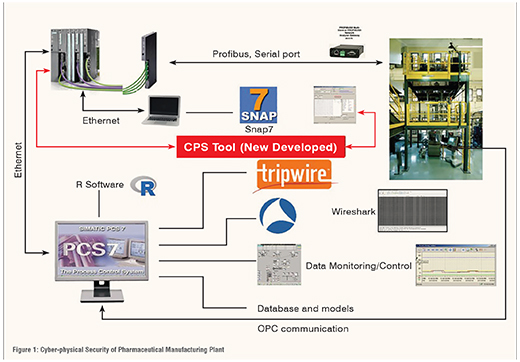
A brief description of some of the cyber security methods and tools needed for cyber-physical security of pharmaceutical manufacturing are given below.
The ease of access to pharmaceutical plants have increased with the advances of automation technology used in industry. Remote operation of the plant via DCS may make manufacture monitoring much more convenient but also opens the risk of vulnerabilities in the network. Network traffic analysers such as Wireshark may use the baseline of the network interface for a specific CPU in order to detect any abnormal activity (Figure 2). The baseline of the network interface is used as a reference in deciding routine traffic. The work station of a pharmaceutical plant should only allow packets of information that are familiar to be exchanged through the network. Wireshark’s role as a network analyser is demonstrated below. (Figure 2)
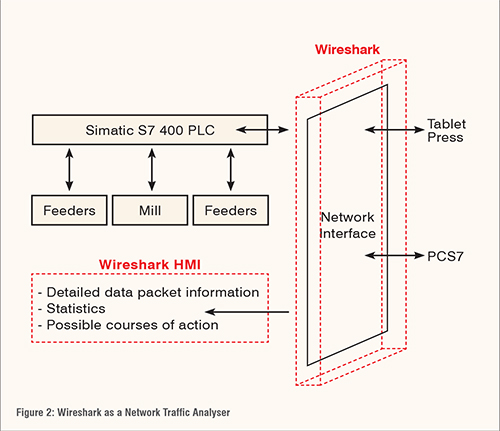
Network protocols are simply different sets of rules of communicating between computers. Setting these rules allows computers to transfer information in practical ways. But different activities on the computer require different protocols. Therefore, identifying protocols is essential to manufacturing operations to ensure only the activities that are allowed are successfully executed. The hypertext transfer protocol (HTTP) for example, in theory, should not be captured in Wireshark because the work station should not be used for browsing the web as mentioned in the introduction.
But simply identifying different protocols is not enough to protect the plant. Additional pieces of information that Wireshark conveniently provide such as the source and destination IP addresses need to be examined as well. In the simplest scenario, an air-tight pharmaceutical manufacturing plant network would only allow exchange of information between the components under the same few IP addresses. Companies may work up to classify other networks that are allowed to communicate with the outside components.
Information exchange through the work station’s Network Interface Card (NIC) would only see traffic to and from these addresses for manufacturing purposes. Once IT engineers build a permitted network system, they now have a foundation of regular traffic that is allowed to pass through the interface. For example, Wireshark’s ability to filter specific IPs can help expose unwanted network infiltration. Filtering is the most basic of Wireshark’s function but also one of the most effective. The number of packets captured in a single analysis is substantial and the filter therefore eliminates ‘noise’ that is useless for seeking undesired packet exchanges.
The sheer amount of data stored in any given computer is nearly incomprehensible to the ordinary person. Data integrity, defined as the accuracy and consistency of stored data, is critical for pharmaceutical companies to keep accurate and credible as outlined by FDA guidelines. Tripwire is a file integrity monitoring tool to capture a baseline of system files and network device configurations. In short, Tripwire uses an authentic reference of the system’s state to continuously seek out any and all changes made in the system. While doing so, it ensures the inevitable changes made to the system are authorised and expected.
SNAP7 is an open source library enabling communication designed for Siemens S7 PLC. It is primarily used in this regard to download data blocks directly from the PLC so that it gives users the ability to monitor and analyse data on multiple layers. The ability to supervise process data on different layers makes potential masking of values less effective for hackers. Reading data blocks gives way for the design of the CPS Tool to directly read information from the PLC without referring to equipment and software HMI where it has been known to be vulnerable to detrimental manipulation.
A new software tool has been developed catered to the needs of a pharmaceutical manufacturing plant. The tool takes advantage of the fact that operators and engineers have the upper hand in manufacturing knowledge. Ultimately, the CPS Tool serves as the defence mechanism most relevant to the continuous pharmaceutical manufacturing pilot plant to date.
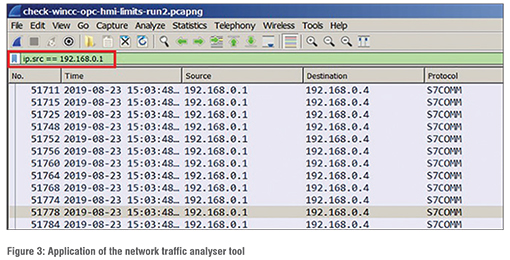
The above mentioned tools have been integrated with pharmaceutical manufacturing plant to protect it from cyber-physical security risk and their performance have been evaluated. One of the applications of the network traffic analyser tool is shown in Figure 3. As shown in the figure, by typing “ip.adr == X.X.X.X” into the filter tool bar, the application will enable the access and security of that network. (Figure 3)
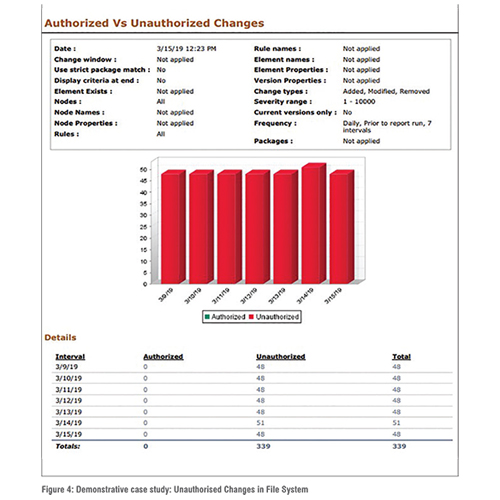
One of the applications of the file integrity tool is shown in Figure 4. As shown in the figure, the authorised and unauthorised access of the work station can be identified using this tool. For demonstration purposes, a baseline was set shortly after download for the application’s reference. It should be noted that, for the demonstration purposes the base line was set purposefully in such a way so that some unauthorised access can be created. Scan frequency was set to daily for seven days. It showed 48 unauthorised changes most days, implying the baseline should be updated or action be taken to stop them. Similarly, the applications of other cyber-physical security tools have been demonstrated for the security of pharmaceutical manufacturing process. (Figure 4)
These methods are some of the most basic strategies employed by many companies worldwide. No matter the amount of resources exhausted into prevention of cyber-physical attacks, those such as Stuxnet and WannaCry continue to show that attackers are often one step ahead in finding network vulnerabilities. For long term safety and success, the pharmaceutical industry must go the extra mile and strive to be proactive.
Conclusions
Existing cyber-physical security measures such as those mentioned previously, and proactive IT teams have proved inadequate against malicious attackers. Pharmaceutical manufacturing plants need to accept that even with advanced cyber security, the human element in the setup of network infrastructures allows gaps, allowing criminals access to the plants. A proposed cyber-physical security tool boosts the defence against an attack by implementing an additional protection layer. The Cyber-physical Security Tool (CPS Tool) may work in the favour of manufacturing plants by customisation of its defence scheme. Utilising inner knowledge of the complex process that is continuous manufacturing provides the upper hand to its users. Inspection of Critical Process Parameter (CPP) data in multiple layers for particular unit operations separately and collectively grants the most complete and authentic view into the manufacturing plant. A novel CPS Tool (developed in house) recognises the advantage of incorporating plant actuators and sensors to curb attempts at maliciously manipulating the system. This is an absolute necessity which should have been implemented in all pharmaceutical manufacturing plants long ago.
Acknowledgements
This work is supported by the National Science Foundation Engineering Research Center on Structured Organic Particulate Systems (C-SOPS), and Siemens Corporation Inc.